Mailing Lists, An Introduction (Free Software Camp 2020)
Main akshay channel | 0 views | 2020-10-10
Website - https://camp.fsf.org.in Announce list - https://lists.fsci.org.in/postorius/lists/camp-announce.mm.gnu.org.in/

Website - https://camp.fsf.org.in Announce list - https://lists.fsci.org.in/postorius/lists/camp-announce.mm.gnu.org.in/

Build video for my custom Network Accessible Storage (NAS) Server Blog Post: https://battlepenguin.com/tech/video/build-a-small-form-factor-storage-server-nas/ YouTube: https://www.youtube.com/watch?v=s8Zed0qJKW4&t=91s

This video is about my teardown of an MSI GS60 laptop, replacing the two internal solid state drives (SSDs) and the trouble I had with backing up and restoring Windows on it. Blog Post: https://battlepenguin.com/tech/video/upgrading-the-ssd-on...
Blog post: https://battlepenguin.com/tech/video/ltsense-using-embedded-python-for-sensor-networks-wellington-python-user-group/ YouTube Mirror: https://www.youtube.com/watchv=Xs7KVfHfoIE

Blog Post: https://battlepenguin.com/tech/video/big-sense-rest-web-services-in-scala-for-sensor-networks-wellington-java-user-group/ YouTube Mirror: https://www.youtube.com/watch?v=S9Gr_LeruWI
Learn how to start collaborating on Write.as with our newest feature, Teams. This will walk you through creating a team, starting a shared blog, and inviting collaborators.
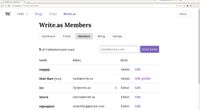
Preview the user role system to be launched with Write.as Teams. Includes these options: * **Admin** -- Has full access to the team and all shared blogs. * **Editor** -- Can see every team member, and has full access to all shared blogs. * **Auth...

I thought I'd do an extra video showing that you can actually view Mastodon and Toot from this, though it is a bit buggy.

Update on my Epaper terminal project. The goal of this project is to be able to build a portable computer with an epaper screen for primarily terminal work that can be used outside in strong sunlight. In the update toot I sent out about a week a...

According to the NIST National Vulnerability Database, 1772 software vulnerabilities with a CVSS score of 7 or higher were disclosed in 2012, and 2013 is so far (at the time of writing) not looking any better. A lot of times the window of e...

I run the internal phishing program at Twitter. It was built from scratch and uses open source tools. It’s custom tailored to our organization. This talk will describe the objective of running an internal phishing program at your organization, wha...
DevSecOps today have extremely powerful tools at their hands: they design and manage all the elements that can prevent a web application from being compromised. Build environment can prevent buggy applications from even being deployed. Protective ...

Docker, Jenkins, network topology, system configuration and software delivery management - all of these are the bread and butter of each DevOps team, but can be also a recipe for a disaster. Walk through the most devastating security failures in D...

Using fast-switching digital hydraulic valves to play notes.
A tutorial to create a new Rust library, compile it as a static library for iOS, and use it in an Xcode project. We then automate a convenient development workflow and explore some of the data types and callbacks that you can use to communicate be...

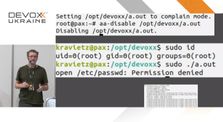
Users are critical part of every authentication scheme, and usability must be treated with just the same respect as cryptographic best practices. Slides are available here https://www.slideshare.net/kravietz/authenticity-and-usability Raw M...

Punking Punkbuster presented by Isaac Dawson at 44CON 2013 in London This presentation will cover the methods and process used while trying to understand how PunkBuster works. From writing custom tools, to coming up with novel ways of overcomin...

Security Lessons from Dictators presented by Jerry Gamblin at 44CON 2013 in London. What do the Grand Ayatollah Seyyed Ali Hosseini Khamenei, Kim Jong-un, Julius Caesar, Abraham Lincoln, Napoleon Bonaparte and Adolph Hitler have to do with netw...

A talk about (info-sec) talks presented by Haroon Meer at 44CON 2013. Last year there was an Information Security conference taking place for almost every day of the year. This translates to about 15 information security talks per day, every da...

Software Security Austerity - Software Security Debt In Modern Software Development. Ollie Whitehouse at 44CON 2012 in London.

Modern Post-Exploitation Strategies. Rich Smith at 44CON 2012 in London.

Speakers: Juergen Pabel Everything to hide This is not a hacking presentation, no vulnerabilities are presented. It's a crash-course in full-disk-encryption ("FDE") concepts, products and implementation aspects. An overview of both commercia...

Building an anonymous Internet within the Internet OnionCat manages to build a complete IP transparent VPN based on Tor's hidden services, provides a simple well-known interface and has the potential to create an anonymous global network which ...

Hacking And Forensics On The Go. Phil Polstra at 44CON 2012.